Schedule
Type | Day | Time | Place | Start | Lecturer |
V3 | Mo | 12:30-14:00 | AH III | April 19 | |
Tue | 08:15-09:45 | AH II | April 20 | ||
Ü2 | Wed | 13:30-15:00 | AH III | April 28 |
News
- (14.10) Points for the second exam can be found here. You may come at 11:00 on Wednesday (20.10) in Room 4203 to check your exam sheets.
- The second exam will take place in AH VI on 27.09, from 13:00 to 15:00.
- (16.08) The updated points for the exam can be found here.
- (10.08) Points for the exam can be found here. You may come at 11:00 on Friday (13.08) at Room 4201b to check your answer sheets.
- (22.07) Points for the exercises.
- (21.07) We provide some example exams and solutions: exam1 (solution1), exam2 (solution2) and exam3 (solution3).
- (14.07) The only allowed materials to take to the exam are a copy of the book, a copy of the lecture slides and a dictionary.
- (14.07) We offer a question session in AH3 on 21.07, after the exercise class.
- (14.07) The exam will take place in AH1 on 30.07, from 13:30 to 15:30.
- (14.07) There will be no lecture on 19.07. The last lecture will be on 20.07.
- (28.06) There will be no exercise class on 30.6. The next exercise will be on 7.7.
- (20.06) The lectures on June 28 and 29 will be cancelled.
- (09.06) New exercise sheet available. Due date 16'th of June.
- (06.06) Exercise lecture from 09.06 is moved to 16.06.
- (06.06) The lecture on June 28 will be cancelled.
- (20.05) Important message for enrolment for the course exam:
Studierende im Bachelor und Master Informatik müssen sich ab diesem
Semester zu Prüfungen über die modularen Anmeldeverfahren in den
*Prüfungsveranstaltungen* in Campus anmelden. Dies gilt für alle
Prüfungen zu Vorlesungen in Pflicht-, Wahlpflicht- und
Anwendungsfachmodulen. Eine Anmeldung nur zur Vorlesung oder Übung
reicht nicht aus. Wichtig: Die Frist für die Anmeldung im
Sommersemester ist *** 28. Mai 2010 ***. Danach ist keine Anmeldung
zu den Prüfungen mehr möglich. - (17.04) For Diplomstudents there is a possibility to take this course for a Theory or "Vertiefungsprüfung" with 4 SWS.
Motivation
 | |
 | |
 |
In 2008, the ACM awarded the prestigious Turing Award - the Nobel Prize in Computer Science - to the pioneers of Model Checking: Ed Clarke, Allen Emerson, and Joseph Sifakis.
Why? Because model checking has evolved in the last twenty-five years into a widely used verification and debugging technique for both software and hardware.
It is used (and further developed) by companies and institutes such as IBM, Intel, NASA, Cadence, Microsoft, and Siemens, to mention a few, and has culminated in a series of mostly freely downloadable software tools that allow the automated verification of, for instance, C#-programs or combinational hardware circuits.
Subtle errors, for instance due to multi-threading, that remain undiscovered using simulation or peer reviewing can potentially be revealed using model checking. Model checking is thus an effective technique to expose potential design errors and improve software and hardware reliability.
Subtle errors, for instance due to multi-threading, that remain undiscovered using simulation or peer reviewing can potentially be revealed using model checking. Model checking is thus an effective technique to expose potential design errors and improve software and hardware reliability.
But how does it work, that is, what are its underlying principles?
That's exactly the focus of this lecture series!
We will show that model checking is based on well-known paradigms from automata theory, graph algorithms, logic, and data structures. Its complexity is analyzed using standard techniques from complexity theory.
Contents of the lecture
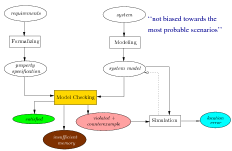 |
Model checking is based on checking models. So, we first start by explaining what models are, and will make clear that so-called labeled transition systems, a model that is akin to automata, are suitable for modeling sequential, as well as multi-threading programs.
This is followed by a detailed study on various classes of system properties such as safety, liveness, and fairness. It will be shown how finite automata as well as variants thereof that accept infinite words are suitable for verifying regular properties.
The linear-time and branching time temporal logics LTL and CTL are then introduced and compared. Model checking algorithms for these logics together with detailed complexity considerations are covered.
Finally, abstraction techniques based on bisimulation and simulation relations are covered. These techniques are at key techniques to combat the state explosion problem.
Prerequisites
This course is suitable for Hauptdiplom, bachelor (this course is part of the "Wahlkatalog" in theoretical computer science), as well as master students.
We expect students to have some basic knowledge in:
- Automata Theory
- Mathematical Logic
- Discrete Mathematics
- Complexity Theory
- Algorithms and Data Structures
The course book (see below) will contain a summary of the issues in these areas that are relevant to this lecture series. We believe that this course is also well-suited for students in electrical engineeering and mathematics.
Follow-up courses
This course provides the basis for the follow-up courses:
Advanced Model Checking
Model Checking Labs
Moreover, it is related to courses such as:
Advanced Model Checking
Model Checking Labs
Moreover, it is related to courses such as:
- Semantics and Verification of Software
- Automata and Reactive Systems (i7)
- Automata on Infinite Words (i7)
- Formal Methods for Embedded Systems (i11)
There are thus plenty of opportunities to combine this course with others! We also regularly offer seminars that are based on model checking and offer various master and diplom theses on model checking and its applications.
Slides and exercise sheets
Date | Lecture | Subject | Slides | Exercises | Solution |
|---|---|---|---|---|---|
April 19 | 1 | Introduction | |||
April 20 | 2 | Transition systems | |||
April 26 | 3 | Parallelism and communication (1) | |||
April 27 | 4 | Parallelism and communication (2) | |||
May 3 | 5 | Linear-Time Properties | |||
May 4 | 6 | Safety and Liveness | |||
May 10 | 7 | Liveness and Fairness | |||
May 17 | 8 | Regular Properties | |||
May 18 | 9 | omega-Regular Properties (1) | |||
May 31 | 10 | omega-Regular Properties (2) | |||
June 1 | 11 | Model Checking with Buechi Automata | |||
June 7 | 12 | Linear Temporal Logic (1) | |||
June 8 | 13 | Linear Temporal Logic (2) | |||
June 14 | 14 | LTL model checking (1) | |||
June 15 | 15 | LTL model checking (2) | |||
16 | Complexity of LTL Model Checking | ||||
June 21 | 17 | Computation tree logic | |||
June 22 | 18 | Expressiveness of LTL and CTL | |||
July 5 | 19 | CTL model checking | |||
July 6 | 20 | CTL with fairness | |||
July 12 | 21 | CTL^+ and CTL^* | |||
July 13 | 22 | Equivalences and Abstraction | |||
July 20 | 23 | CTL, CTL^*-equivalence |
(*) means that the file has been updated.
The solutions are accessible within the university network with the credentials given in the exercise class.
Materials
 |
The lectures and all materials are in english. The slides will be made available via this webpage during the course.
The course is based on the recently published book:
An errata document to the book may be found here.
It is possible to buy a book (about 40 euros), but there is no need to do so as there are various copies of the book available at the CS library.
- E.M. Clarke, O. Grumberg, D.A. Peled: Model Checking, MIT Press, 1999
- M. Huth and M.D. Ryan: Logic in Computer Science - Modelling and Reasoning about Systems, Cambridge University Press, 2nd edition, 2004
- K. Schneider: Verification of Reactive Systems, Springer-Verlag, Texts in Theoretical Computer Science. An EATCS Series, 2004

